In the 1980s, when the Internet was very new in networking and worldwide use, the term “firewall” was utilized in network technologies. ACLs were used for network protection before firewalls (short for access control lists).
They were on routers and decided whether access to unique IP addresses could be given for the network. But because ACLs can not analyze the existence of blocked packets and are not sufficiently efficient to stop attacks from the network, it develops a firewall. Below, the creation of firewalls and the forms, how they function and the advantages of using firewalls have been clarified. Let’s begin with the key thing.
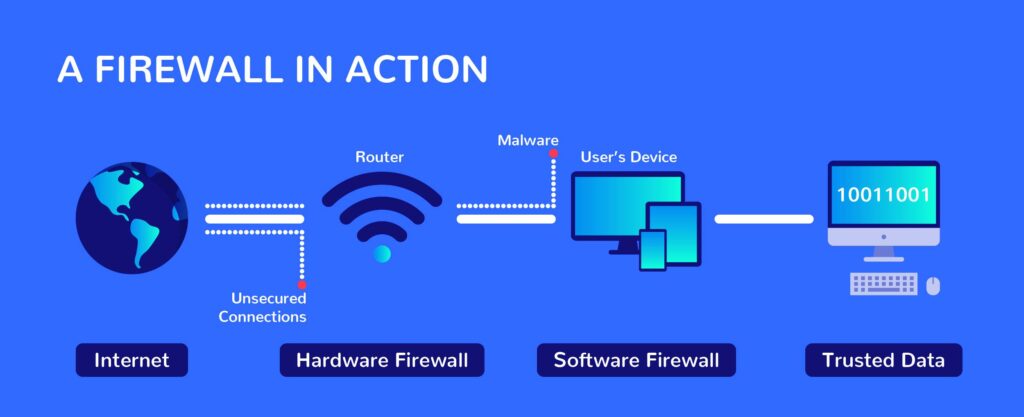
What is a Firewall?
Definition: A firewall is a device intended to block unwanted access to or from a private network. Definition: In other words, unauthorized Internet users are prohibited from accessing the internet’s private networks, in particular intranets.
The firewall is not always a standalone system, but it does combine servers or routers with software to ensure stability. You may mount the firewall in, or in conjunction with, software or hardware.
The deployment should be carried out in such a way that all incoming/outgoing packets are transferred through the firewall through the local network (Intranet).
How does a firewall work?
Each block of data packets in or from the intranet or host device is scanned by the firewall. A firewall can do three things on the basis of a certain set of security rules:
- Accept: Allow data packets to be transmitted.
- Discard Unresponsive packets stack.
- Reject: Give an “unreachable bug” to the source, then block the data packets.
Let us take the example of a medium-sized business employing a thousand workers. Let’s say it’s a hundred machine IT business, all linked via the cards. To connect these machines to the external network (the Internet), the organization requires at least one connexion. Let me claim that line X1 links the Internet to the internal network (Intranet).
In this case, an X1 firewall (and/or on every device on the intranet) must be installed by the organization. All these machines are vulnerable to external threats without a powerful firewall. If one of the workers errs and leaves a security breach, attackers will (on the Internet) check out the hole in order to connect to internal computers. But they can stop dangerous traffic with a firewall in place. For eg, if the company wishes not to authorize FTP connexions, the firewall blocks all public FTP traffic from and to the external network.
Firewalls can be split into two categories into different firewalls:
Firewalls from servers and firewalls from the network. Each firewall has its own benefit and drawbacks, although both play an important role in safekeeping your data secure.
Host-based firewalls are mounted in and out of the machine directly in the machine to handle the data set. It may be an agent or operating system program that operates in the background. On the central, wide area networks and intranets,
Firewalls are located. You philter data from two or more networks. There may be computer machines or applications operating on general machines.
There are various types of firewalls that shield networks and host machines from varying degrees of security. The most popular ones were clarified by us:
1. Stateful filters
Static philters are firewalls built in the late 1980s for the second generation. They track the working condition and the characteristics of the moving network connexions.
In particular, state-of-the-art philters register the IP and port addresses involved and the packets crossing the connector. They will therefore research individual conversations between two endpoints. These are vulnerable to DoS attacks, however, involving the flooding of the target system with redundant requests to overwhelm the host machine and avoid the making of valid requests.
2. Packet filters
The first-generation firewalls are packet philters. The data packets sent between computers are being analyzed. If a firewall does not satisfy the filtering requirements, it either ignores or drops the packet.
It is often referred to as a network layer firewall since it operates at the lower layer of TCP / IP (a series of Networking Protocols used on the Internet). For example, a firewall is used with FreeBSD, Linux, Linux, and Mac OS X, iPad tablets are used with Linux, NPF with NetBSD, and Mac OS X with PF (> 10.4).
3. Application firewalls
Web firewalls are firewalls of third-generation that provide unique programs and protocols like HTTP, DNS, and FTP. It functions as a firewall extension, delivering facilities right up to the application layer (the top layer of the OSI model). It operates by decoding the data packet operation ID according to the data transfer rules for a local network or host.
The firewall attaches to sockets to philter connexions in the OSI model between app layers and lower layers. Some of the services that implement firewalls perform include data collection, program execution, malware blocking, and more. Modern device firewalls can also download server encryption, consolidate authentication, and block protection policy-related material.
4. Next-generation firewall
A next-generation firewall is an advanced application firewall that combines a traditional firewall with other filtering functions for network devices. Its aim is to allow more OSI model layers and to boost network traffic filtering based on packet information.
In brief, next-generation firewalls have many additional capabilities such as automated avoidance of attack, cloud-based risks, and device warnings, and control. You use a more comprehensive management style by analyzing the payloads for ransomware, exploitable attacks, and malicious behaviors in packages and related signatures.
5. Proxy
An IP address and data transfer can also be shielded by a proxy server as a firewall. It is mostly used for users ‘and local machines’ anonymous requests. Contrary to standard firewalls, application-level proxy servers philter network traffic. They detect traffic in Layer 7, for example, FTP and HTTP, and analyze traffic malicious with stateful and comprehensive packet monitoring.
Modern proxy servers provide enhanced efficiency (catching resources requested) and correction of errors (by correcting errors automatically on proxy contents) in addition to protection.
6. Translation of network addresses
Another issue emerged as firewalls became popular: the amount of IPv4 addresses available declined with the possibility of depletion. In order to resolve the issue, researchers have identified numerous pathways. Network address translation (NAT) is one such mechanism.
When they pass via the traffic routing unit, NAT converts the IP address space by changing details on a network address within an IP packet header. This helps the same IP addresses in various areas of the Internet to be replicated.
NAT embraces the main protocols (like email and web browsing) used to navigate the Internet every day by billions of consumers. It has become common because it minimizes the need for global, low configuration Internet addresses.
Advantages in Firewall systems
Benefits The intruders who wish to reach your network/device are still connected to internet networks. Together with an anti-virus tool, firewall policies improve your system protection. You detect and secure malware, Trojans, worms, and spyware from your computers. You have reduced the chance of spying on you through keyloggers.
Firewall systems provide a range of useful features for the internet as well as filtering malicious traffic. For eg, you can service your network as a DHCP or VPN server. Firewalls are highly sophisticated with modern hardware. They can rely on higher knowledge in the near future so that they will be conscious of circumstances. Artificial information helps firewalls, without interfering with contact between devices, to more aggressively target intruders.



